How does HTTPS protect data and how can I install it?
The HTTPS protocol is rightfully considered the key technology of the modern Internet and a real must have for any site that cares about the security of the personal data of its users. In our new article, you will read about what HTTPS is, how it differs from another popular HTTP standard, how it works, why you need it, and how to implement it on your website?
Content:
1. HTTPS - what is this protocol?
2. How does a secure HTTPS connection work?
3. Types of SSL certificates
4. Why and who needs HTTPS data encryption?
5. Conclusion: HTTPS - secure connection to the site
HTTPS - what is this protocol?
HTTPS is a secure Hypertext Transfer Protocol that enables encrypted communication between a site server and its users. SSL / TLS protocols are used as encryption tools in this standard, which protect information using cryptographic methods.
As you know, the Internet is based on the HTTP - Hypertext Transfer Protocol. This is a technology for exchanging data between a client (user) and a server (site): the client sends a request to the server and thereby initiates an Internet connection. The server receives the request, processes it and returns the result to the client, allowing you to open the site or perform any action on it.
In the process of exchanging data between the client and the server, information can become available to third parties: from intruders-hackers (who want to purposefully take possession of it) to an Internet provider or network administrator. To eliminate such risks, the HTTP protocol was improved - a special extension for encrypting the connection was added to it, after which it was named HTTPS (secured). Encrypted communication goes through port 443, while unsecured HTTP uses port 80.
Thus, HTTPS is not a separate new protocol, but the same classic HTTP protocol, but protected by cryptography. It provides three important principles, allowing data to be encrypted (protected from eavesdropping), saved (committed to any changes), and authenticated (prevented from client redirection). These are the very same 3 levels of protection, thanks to which HTTPS has become a prerequisite for the security of any modern website.
How does a secure HTTPS connection work?
When a user enters a site address, their browser sends a request to the site server to provide their SSL certificate. In response, the server sends a certificate, after which the browser verifies it with the certification authority. At the next stage, the browser and the server "agree" to encrypt the connection using a common one-time asymmetric key, which is generated automatically every time you enter the site. As a result, the secure HTTPS communication between the site and the visitors' browsers is encrypted with cryptography. Even if someone outside intercepts this data, they will not be able to use it, since it is transmitted in the form of a cipher.
- Automate the work of an online store or landing
- Empower through integration
- Don't spend money on programmers and integrators
- Save time by automating routine tasks
The most important factor in the reliability and security of HTTPS is considered to be the site certificate authentication - SSL authentication. In order to make your site secure, its owner must obtain an SSL certificate and then upload it to the server. It is issued by special certification authorities, and they also verify the certificate when requested by users' browsers. Without SSL verification, it is considered invalid - if the browser does not receive confirmation from the certification authority, it will simply not allow the user to visit this site.
After purchasing and installing the certificate, the owner must configure redirecting visitors from HTTP to the HTTPS version of the site. This can be done through the settings of the hosting provider or by editing the .htaccess file hosted on the server. It is equally important to notify search engines that your site has switched to the HTTPS protocol in order to avoid a temporary drop in its ranking in the search results. To do this, you need to add the HTTPS domain address to Google Search Console, marking it as the main version of the site. Google recommends additionally using HSTS technology for such sites. At the end, you need to register the HOST address of the HTTPS site in the robots.txt file.
Types of SSL certificates
Today there are several types of SSL / TLS certificates:
- DV. These are the most basic free certificates and most often come bundled with your domain. They are issued instantly and require basic verification of site ownership via e-mail or http. DV certificates contain information about the encryption algorithm, their expiration date and the certificate authority that issued them. They are issued to anyone who wants to without confirmation of their identity, most often they are used by simple sites or blogs.
- OV. These are more secure, paid certificates and must be ordered separately. Their main feature is the verification of the company that owns the site, so the OV-certificate can only be obtained by a legal entity. During their registration, the authenticity of the ordering company is verified, which is why the period for issuing OV-certificates is from two days. They differ from DV certificates by the presence of company information in the certificate verification menu in the browser address bar.
- EV. These are certificates with extended validation, which are also issued only to companies and require more serious verification than OV certificates. This type of SSL is considered the most reliable, and you can recognize it on the site by the name of the owner company against the background of a green strip that is displayed in the address bar of the browser.
- Wildcard and SAN. Such SSL certificates are optimal for sites with several subdomains, while ordinary DV / OV / EVs are valid for only one domain.
Why and who needs HTTPS data encryption?
So, we learned what HTTPS is and how it protects user data, but what benefits does it provide to site owners and who needs it?
If the activity of your site is related to the processing of personal or, moreover, financial data of users, then you are obliged to ensure their protection - otherwise you will not be trusted. For example, many visitors will not even dare to register (enter a username and password) without a secure connection to the site, not to mention the fact that in order to indicate there the numbers of their bank card to pay for goods.
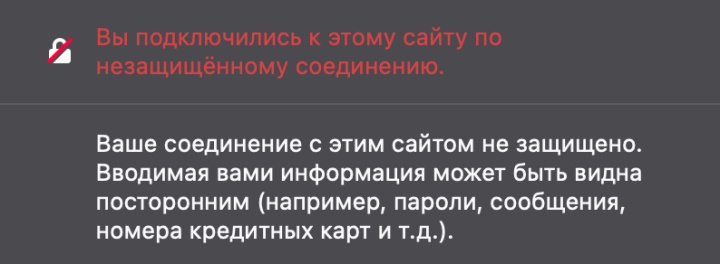
Moreover, modern Internet browsers carefully monitor the presence of an SSL certificate for sites. When trying to open a site without HTTPS, any browser (Google Chrome, Mozilla Firefox, etc.) will first warn that the connection will be unencrypted and its data may become available to strangers.
The presence of HTTPS also has a positive effect on SEO optimization: search engines take into account the presence of an SSL certificate, so having a secure connection is an important factor in site ranking.
Conclusion: HTTPS - Secure Connection to the Site
HTTPS is an enhanced version of the Hypertext Transfer Protocol (HTTP) that helps encrypt data transmitted through it. It ensures the secure connection of users to the site and protects their personal and financial information.
To switch to HTTPS, the site owner must obtain and download a special SSL / TLS certificate, which has several varieties with different degrees of protection. The HTTPS protocol is an almost mandatory standard for modern sites, especially online stores or other sites with user registration and online payment options.
Time is the most valuable resource in today's business environment. By eliminating routine from work processes, you will get more opportunities to implement the most daring plans and ideas. Choose - you can continue to waste time, money and nerves on ineffective solutions, or you can use ApiX-Drive, automating work processes and achieving results with minimal investment of money, effort and human resources.